For most Americans, the first they heard of using a vehicle to attack and kill people was in Charlottesville, VA, in 2017 when a man drove his car into anti-white-supremacist protestors, killing Heather Heyer and wounding dozens of others. But Charlottesville was just the tail end of a movement that has killed people across the globe.
For Europeans and those in the Middle East, vehicle ramming attacks (VRAs) is a familiar tactic. In fact, according to the Global Terrorism Database, vehicle borne attacks date to the 1970s but accelerated after Hamas’s 2014 attacks against Israeli targets. It was quickly picked up by Al-Queda and Isis as a low-cost, high-profile method to terrorize civilians. It was then exported into Europe and now it is a key tactic used by domestic terrorists around the world.
Definition
The Department of Homeland Security (DHS) defines such attacks as deliberately aiming a vehicle intending to inflict fatal injuries or cause property damage.
“This tactical evolution is a microcosm of the broader tectonic shifts in today’s terrorism threats,” said Mia Bloom, author of Dying to Kill, in a recent piece. “Just as vehicle ramming has migrated to right-wing and extremists, so, too, has the thrust of today’s terrorism threat, especially as these groups absorb more and more tactical [lessons] from terrorists such as jihadists,”
Vehicle Ramming Potential Indicators
The use of vehicles as weapons often has few or no observable indicators but identifying and reporting suspicious activities may assist in detecting a potential vehicle-ramming attack plot. Any one of these activities may be insignificant on its own, but when observed in combination with other suspicious behaviors — particularly advocacy of violence — they may constitute a basis for reporting.
• Reported theft of large or heavy-duty vehicles.
• Observed difficulty in explaining the planned use of a rented vehicle.
• Exhibited nervousness during vehicle rental discussion and insistence on paying rental fees in cash.
• Inability to produce required documentation, such as a valid driver’s license or appropriate endorsement for the class of vehicle sought.
• Observed difficulties in operating a rented vehicle, such as large or heavy-duty trucks, indicating a lack of familiarity from prior usage or experience.
• Loitering, parking, or standing in the same area over multiple days with no reasonable explanation.
• Unexplained use of binoculars, cameras, and recording devices.
Homeland Security Vehicle Ramming – Action Guide

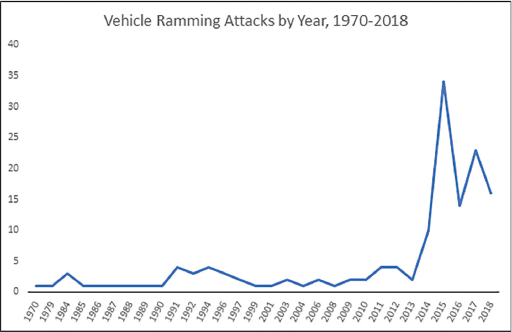
The database contains records of VRAs from both air and ground vehicles showing 146 terrorist incidents with cars, vans or trucks between 1970 through 2018.
The publicity surrounding Hamas attacks prompted a wave of attacks in the US, Sweden, Austria, Spain, Germany and the UK, according to the Pandora Report.
Since May 2020 there have been 104 incidents in the US mostly targeting the Black Lives Matter movement, according to Ari Weil, deputy researcher with the University of Chicago’s Project on Security and Threats.
Rentals Used in Attacks
While the majority of attackers use their personal vehicles, nearly half rent, illustrating the advanced planning in play.
Timothy McVeigh rented a Ryder truck to execute his destruction of the Murrah building in Oklahoma City in 1995. So, too, did those who planted the truck bomb at the World Trade Center in 1993. A man, now serving a life sentence, booked a van weeks earlier for his 2018 Toronto van attack, which killed 10 and wounded 16.
The use of rental vehicles prompted the Department of Homeland Security (DHS), Transportation Security Administration (TSA) and Federal Bureau of Investigation (FBI) to partner with the Truck Renting and Leasing Association (TRLA) and the American Car Rental Association (ACRA) to produce a training video for rental companies. The FBI, TSA and DHS declined to participate in this story.
Mike Sullivan, then assistant director of the Office of Private Sector with the FBI, appears in the video describing red flags which mirror the behavior of would-be skyjackers — nervousness, evasiveness, inconsistent story, no or bogus identification and paying in cash.
Brian Harrell, who was at the time the video was made assistant secretary for infrastructure protection at DHS, cited statistics from the Consortium for the Study of Terrorism and Responses to Terror (START), a DHS Center of Excellence in its Science and Technology Directorate.
“In the two-year period 2016 and 2017, there were 19 vehicle-ramming attacks against innocent civilians around the world, injuring over 650 people and killing an additional 127,” he said in the video. “In nearly 40% of those attacks, the vehicle was rented from a vehicle rental company.”
Such statistics probably underestimate the problem since many go unreported. One such incident is chilling and illustrates the randomness. Minneapolis protestors heading home encountered a man in an SUV who motioned he would wait for them to cross the street. However, as soon as they were in front of his car, he sped up and they narrowly missed being hit.
Difficulty in Profiling Attackers
“We have seen a few different types of individuals carrying out these kinds of attacks,” Countering Violent Extremism (CVE) Research Analyst Josh Lipowsky told Transportation Security International. “In Europe, these attacks have largely been perpetrated by adherents of radical Islamism. In the United States, we have seen people with multiple viewpoints utilize vehicle attacks, most notably Islamists, white nationalists and the far left.”
The growing use of vehicle ramming is not just aimed at large events. Many attacks kill and maim those just going about their daily activity such as in the 82-second attack at Westminster Bridge in London in 2017 when an attacker in a Hyundai Tucson ploughed down pedestrians and bicyclists before crashing into security barriers outside the Houses of Parliament.
An Epidemiological Approach
Nor do VRAs necessarily have to be part of an organized offensive.
For instance, on Halloween 2017 eight people were killed and 11 wounded in New York City by an Islamic sympathizer when he drove a rented truck onto a popular bike path.
What Should People Do in Case of a Vehicle Ramming Attack?
What Should People Do in Case of a Vehicle Ramming Attack?
• Run to the nearest safe area while moving away from the source of hazard.
• If a fall occurs, curl into a protected position and try to get up as soon as possible to avoid being trampled.
• If no rapid escape is possible, seek cover behind any available natural or artificial objects that eliminate direct line of sight from the source of hazard.
• Call 9-1-1 and remain alert for potential secondary attacks.
• Render first aid when safe to do so.
• Maintain situational awareness while providing assistance to others.
• When help arrives, follow instructions given by law enforcement and first responders.
Homeland Security Vehicle Ramming – Action Guide

“VRAs differ from many more conventional attacks because individuals who carry out these attacks often tend to be more self-starters who have often been radicalized and encouraged to carry out the tactic but frequently are not acting under direct orders from a given group,” Assistant Professor at the School of Advanced Military Studies Dr. Jacob Stoil explained to TSI, noting that he is speaking from his own research and not as a government official.
“I noticed a pattern of tactical dissemination of such attacks that highly resembled the spread of disease,” said Stoil.
“At King’s College London, I had the opportunity to study under Profs. Edgar Jones and Simon Wessely who were doing pioneering research into psychiatric epidemiology and how psychiatric problems spread communicably. The patterns I saw followed fairly closely to epidemiological models.”
“At King’s College London, I had the opportunity to study under Profs. Edgar Jones and Simon Wessely who were doing pioneering research into psychiatric epidemiology and how psychiatric problems spread communicably. The patterns I saw followed fairly closely to epidemiological models.”
Significant media coverage is a warning sign security professionals need to be on alert and prepare.
For instance, a Seattle man rammed his SUV into protestors in Seattle last July 4th, which was followed by two others in Indiana, one within hours, the other within two days. In addition, such attacks are often part of a multi-pronged strategy in which the perpetrator uses other weapons to continue the attack on foot.

“A vehicular attack is easy for anyone to launch with little or no planning,” said Harrell. “Active shooter tactics target crowds who are contained, vehicle ramming tactics are not hampered by this. Crowds of people are ubiquitous in every city, regardless of holidays, special events or general workdays.”
In the deadliest modern vehicular terrorist attack in Europe, a Tunisian-born man drove a 19-ton truck into a crowd celebrating Bastille Day at Nice’s Promenade des Anglais, killing 86 people and wounding more than 430 others, CEP reported in a study on the 2016 attack.
“ISIS claimed responsibility for the terrorist attack two days later, calling [the driver] a ‘soldier of the Islamic State,’” the Counter Terrorism Project said in its report. “The attack in Nice…launched a wave of terrorist and ISIS-claimed vehicular attacks around the world including Vienna, Ohio, Berlin, London, Antwerp, Stockholm, Paris, Barcelona, Edmonton and New York.
VRAs, experts say, are a poor man’s weapon of mass destruction since no assembly is required, unlike bombings.
“My research shows that ISIS was able to train children as young at 12 to ram their explosive laden vehicles into fixed targets,” said Bloom.
Harrell, who moved to the private sector since making the DHS/FBI video, agrees.
“Attacks of this nature require minimal capability but can have a devastating impact in crowded places or streets and tend to be successful as they minimize the potential for pre-attack detection,” he said.
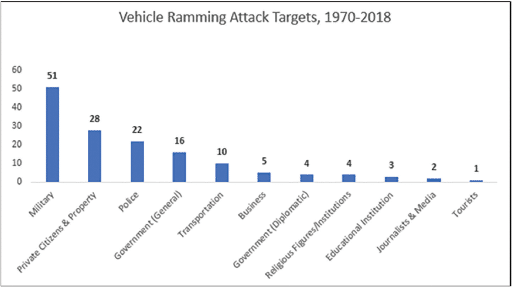
“Since the 2017 Unite the Right rally in Charlottesville, we have seen the far right adopt this tactic as well as a method of pushing back against and delegitimizing civil rights protesters,” Lipowsky said. “The propaganda we’ve seen in the white supremacist space promoting vehicular attacks seeks to dehumanize the victims, painting victims – often protesters – as inconveniences preventing people from carrying on with their normal routines. This propaganda then legitimizes violence as a method of removing that impediment.”
That white-supremacist space spreads memes about VRAs adding the hashtag “all lives splatter,” or calling protestors “speed bumps.” Slate reported one meme – “Run Them Over” became popular against Black Live Matter and protests against the Dakota Access Pipeline.
In what should not be a surprise after the revelations police enthusiastically participated in the January 6 attack on the Capitol building, law enforcement are also the perpetrators, according to Weil who pointed to seven incidents. Police and even government officials have shared memes on police message boards encouraging more attacks.
That complicates determining motivation and whether police were using an accepted police tactic for defending themselves or whether or not the situation warranted the use of police ramming.
On the other hand, police are also targets. “Far-left propaganda has specifically targeted police officers, using – for example – slogans like ACAB (All Cops Are Bastards) and calling for attacks against perceived villains in the name of social justice,” said Lipowsky.
“Some segments of the far left have also adopted the tactic to strike against authority, specifically police officers. In several of last summer’s protests, we saw individuals attacking officers with their cars.”
“Some segments of the far left have also adopted the tactic to strike against authority, specifically police officers. In several of last summer’s protests, we saw individuals attacking officers with their cars.”
Examples include a May 2020 incident in Atlanta when a protester on an ATV struck and wounded a police officer during protests. In early June 2020, three officers in Buffalo, NY, were struck and wounded by a vehicle during protests. In June, protesters in Detroit surrounded a police SUV and began climbing on top of it, leading the officers to strike protesters.”
Neo-Nazis Want Civil War
There is also another undercurrent – using VARs to prompt a race war. “Neo-Nazi groups that adhere to the accelerationist ideology – that a race war is inevitable and should be accelerated – follow a dogma of death by a thousand cuts,” Lipowsky explained. “They want to see more individuals carry out these attacks to trigger a race war that creates a pure ethnonationalist society.”
While there are extremists on both sides, said Lipowsky, the far right is much more organized, has more propaganda promoting these kinds of attacks and is responsible for more attacks.
“The far left has not been as prolific as the far right or Islamists in utilizing this tactic,” he said. “Unlike the far right, the far left is much less organized, and attackers are not widely lionized to the extent they are on the far right. While we do not see organizations like Antifa directing people to attack police officers, we do see individuals who subscribe to various interpretations of these ideologies promote violence, including vehicle attacks.”
Lipowsky also said the far left has no overarching, unifying manifesto to which all antifa groups adhere. It is very disparate groups with differing tactics and ideologies all operating under the broad label of antifa.
“Without that hierarchal structure and support, you’re more likely to see individuals make snap decisions in service of the broader ideology using the tools they have at hand to strike at symbols of authority, which they interpret to be symbols of fascist oppression,” he said.
Mitigation Strategies and Protective Measures
Physical Security
• Post signage relating to emergency entry and exit points, first-aid stations, and shelter locations.
• Define the perimeter and areas that require access control for pedestrians and vehicles.
• Restrict all vehicular traffic through controlled and secure “pedestrian-only” areas, including separate ingress and egress routes for delivery vehicles away from events.
• Use remote parking and shuttle services to keep vehicles away from critical assets or mass gatherings.
• Establish clear standoff zones. Bollards, heavy planters, and barricades can be used to increase standoff distances between large crowds and vehicles. It is important to ensure that these architectural solutions are appropriately sized, adequately anchored, and purposely reinforced against impact loads.
• Evaluate the need for vehicle barriers, considering passive barriers (fixed bollards, fences, jersey barriers, etc.) and/or active barriers (retractable bollards, rising wedges, etc.).
• If appropriate, pre-position heavy vehicles to serve as physical barriers around the perimeter of densely populated locations.
Access, Planning, and Personnel
• Review personnel files of recently terminated employees to determine whether they pose a security risk.
• Evaluate vehicle traffic patterns near the venue and implement strategies to reduce vehicle speeds and improve pedestrian safety.
• Conduct a site assessment prior to holding an event that identifies vulnerabilities. For example, the driver of the vehicle may not necessarily follow traffic rules (e.g., one-way street), which must be taken into account when developing a strategy.
• Devise credential systems that indicate areas of access and purpose of activity on the premises.
• Monitor all vehicles approaching an entrance or gathering of people for signs of threatening or suspicious behavior (e.g., unexpected truck traffic, unusual high speed, vehicles riding particularly low).
• Design a monitoring, surveillance, and inspection program that is consistent with venue operations and associated security requirements. If surveillance cameras are used, train personnel to interpret video footage and identify potential security-related events.
Homeland Security Vehicle Ramming – Action Guide
Profiling Attackers
“Terrorist groups like al-Qaeda, Isis and Hamas have long called for – and claimed responsibility for – vehicular terrorist attacks,” Lipowsky explained. “In Europe and the Middle East, we’ve seen the large majority of perpetrators are affiliated with radical Islamist positions. As such, these groups do not need to make significant investments to prepare for such attacks or be involved in the planning. All they need to do is claim the attacker as a soldier for their cause and they get the publicity without the work. We often see such attackers leave behind declarations of allegiance to one of these groups, but we have also seen ISIS claim individuals as their soldiers if the perpetrator dies in the attack. Then it becomes a race for these groups to stake their claim first.”
Whack-A-Mole
If social media is the vector for the spread of this disease, then it is also part of the solution, according to experts. That is easier said than done because, like a virus, these groups adapt to find other pathways when locked out of mainstream channels. More importantly, racist memes have migrated to mainstream Republican and conservative media.
Working with social media companies to dismantle the online content of terrorist groups has been a difficult strategy especially since they came so late to the effort.
“Several social media companies have made great strides to identify and remove propaganda from their platforms, but more must be done,” said Lipowsky. “We’ve seen some companies take steps to remove content as it’s reported, but there is so much out there. Automated systems can either miss targets entirely or ignore context, such as a Facebook post automatically being removed for quoting a jihadist figure in the context of raising awareness. Users need to immediately flag violent content on these sites, while the tech companies need to invest in a human element to monitor their platforms to ensure accuracy and swiftness in removing objectionable content.”
Lipowsky noted barring content has only driven it underground on encrypted platforms more difficult to monitor. Gab, Parler, 4chan and 8kun are all sites catering to the extreme right and flout international conventions against such content such as the Global Internet Forum for Counter Terrorism (GIFCT), a collaboration between the technology industry, government, civil society and academia to counter terrorism and violent extremism online.
“Unfortunately, there isn’t really a solution for that,” said Lipowsky. “As long as these ideologies exists, people will seek ways to skirt restrictions, even as the larger platforms take more active roles in removing inciteful propaganda. We saw this with Gab, which briefly went down in 2018 after pressure on its internet service provider because of the number of anti-Semitic posts on the platform but it soon returned. Gab was one of the platforms used to plan the Capitol assault. The unregulated nature of the dark web allows for the growth of underground forums. As we saw with the Silk Road platform on the dark web several years ago, mirror sites go up as quickly as they get taken down and it becomes a game of Whack-a-Mole.”
“Unfortunately, there isn’t really a solution for that,” said Lipowsky. “As long as these ideologies exists, people will seek ways to skirt restrictions, even as the larger platforms take more active roles in removing inciteful propaganda. We saw this with Gab, which briefly went down in 2018 after pressure on its internet service provider because of the number of anti-Semitic posts on the platform but it soon returned. Gab was one of the platforms used to plan the Capitol assault. The unregulated nature of the dark web allows for the growth of underground forums. As we saw with the Silk Road platform on the dark web several years ago, mirror sites go up as quickly as they get taken down and it becomes a game of Whack-a-Mole.”
Defense Against Attacks
If little can be done about preventing the random attacks on civilians, there are things authorities can do.
“Unfortunately, vehicle rammings do not require advance planning or financial investment and they are effective and simple,” said Lipowsky. “Because of this, they are difficult to prevent until the final moments. They are not always clearly identified when they are happening, which affects how law enforcement responds in neutralizing the driver to prevent further casualties. It is not always immediately clear whether an out-of-control car is a deliberate attack or a driver who has lost control due to brake failure or a heart attack.”
He sees the answer in attacking the ideology that drives it by increasing community intervention and education programs.
“Whether it’s radical Islam or white nationalism, education is the only way to ultimately defeat these extremist ideologies,” said Lipowsky. “At the same time, we can take steps to harden targets to make it more difficult to carry out these types of attacks.”
Public Hypervigilance
Stoil said there are four general ways to counter VRA threat – deterrence, detection, prevention, and protection. Deterrence involves changing the risk-reward calculus and making the risks of the attack much higher than the anticipated reward. This was the case with airplane hijackings, common in the 60s and 70s. Systems were put in place that changed the risk-reward calculus and you don’t see these tactics used frequently now. Detection for VRAs might not have significantly different components than the process which already exist to detect terrorist threats.
Finally, protection might include assessing high-profile areas, anticipating targets and creating permanent or semi-permanent structures that would limit the success of VRAs.
But hardening even high-profile targets is no guarantee as evidenced on April 2 when a lone driver ploughed into and killed one Capitol police officer, wounding another at the Capitol complex.
“Security personnel and law enforcement must be prepared for evolving terrorist tactics that remain unconventional but are simple and easily supported logistically,” Harrell advised. “Organizations should consider establishing clear standoff zones. Bollards, heavy planters and barricades can be used to increase standoff distances between large crowds and vehicles. It is important to ensure that these architectural solutions are appropriately sized, adequately anchored, and purposely reinforced against any impact loads.”
Called defensive landscaping, these measures include lining roads with trees or using reinforced planters around public areas such as open-air markets and public squares. Temporary structures could be as simple as cordoning police vehicles around festivals, concerts or protests. In the future it will have to ensure that safety protocols are in place as vehicles become more autonomous.
The best strategy for the public is situational awareness whether alone or in a crowd. Women have long known they must constantly check their surroundings as they walk, looking to their right or left and using peripheral vision to check behind them to enhance their safety. That must now be extended to anyone gathered peacefully, or, as in Toronto, New York or Nice, just going about their daily routine.
“The number one thing the public should know is to be vigilant,” Lipowsky advised. “If something feels amiss, it’s always better to report it and check it out than to let it go. Nine times out of 10 it may be nothing but preventing that one case is worth the time and effort of nine false alarms.”
